UKG has released security updates that will go into effect in September of this year. In this announcement, you’ll find detailed information, instructions, and FAQs.
Overview of the Security Updates
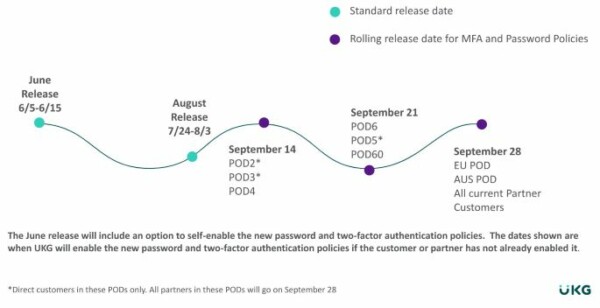
MFA and Password Policies Release Calendar
Security Updates
To add additional layers of security, UKG will require most users to use Multi-Factor Authentication* (MFA) to login into the application.
- MFA is a security protocol that requires more than one method of authentication
- MFA creates additional layers of validation to prevent unauthorized access
- Two-Factor Authentication is a type of MFA which requires two layers to access
UKG will provide default policies based on best practice recommendations. The policies available:
- Authentication Policy
- Password Policy
- Two-Factor Policy
If your organization is using Single Sign On (SSO) these policies do not apply to you.
Password and Two-Factor Policies
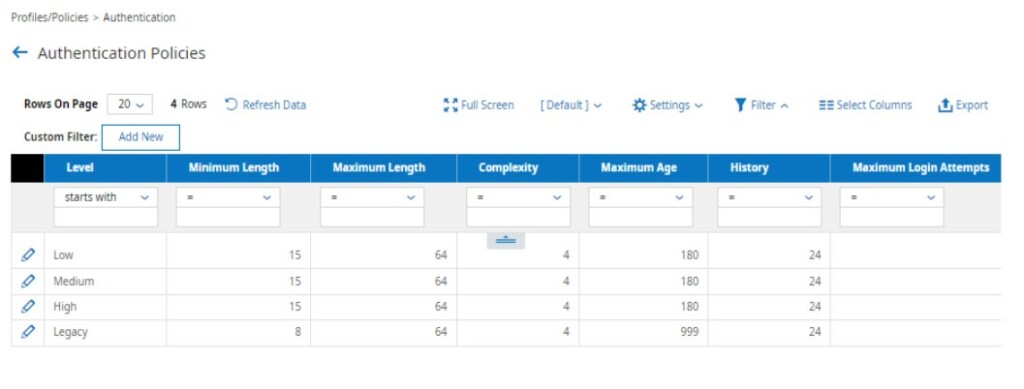
Authentication Policies
The configuration of the password and two-factor policies is completed within the Authentication policies.
The Legacy Authentication Policy is used for the old password and two-factor preferences.
The Low, Medium and High policies are used with the new password and two-factor preferences.
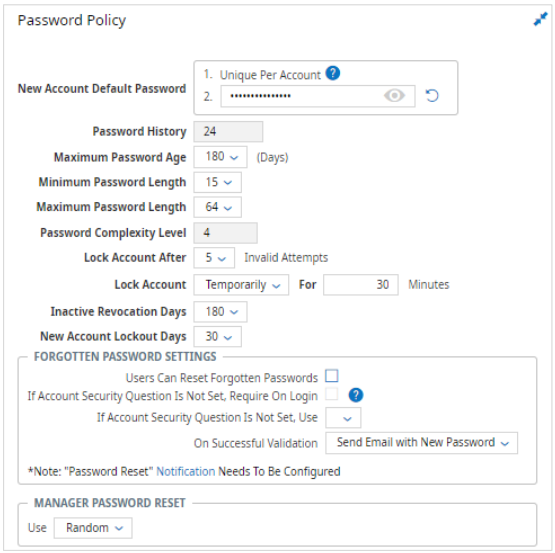
Password Policy
New Account Default Password now has two options:
- Unique Per Account
- Custom
Manager password reset now has two options:
- Random
- Custom
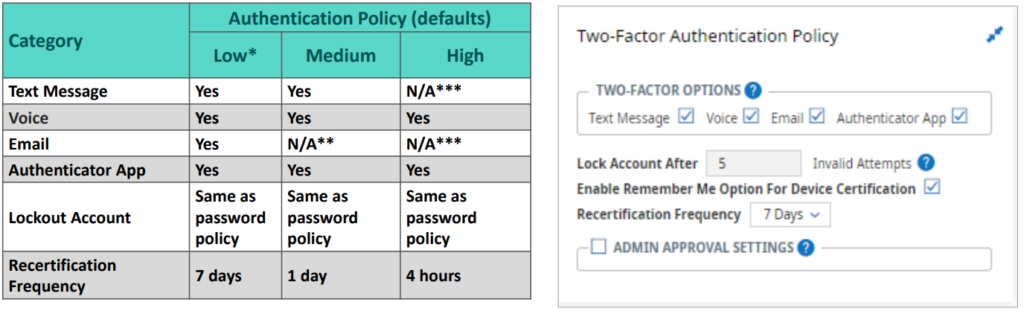
Two-Factor Authentication (2FA) Policy
*Low – two-factor authentication can be turned off for users assigned to the Low policy by unselecting all 4 two-factor options
*Medium – Email is not an option. The field will be read only and cannot be selected
***High – Text Message and Email are not options. The fields will be read only and cannot be selected.
Security Profile and Authentication Level
Authentication Policy Level – Security Profile
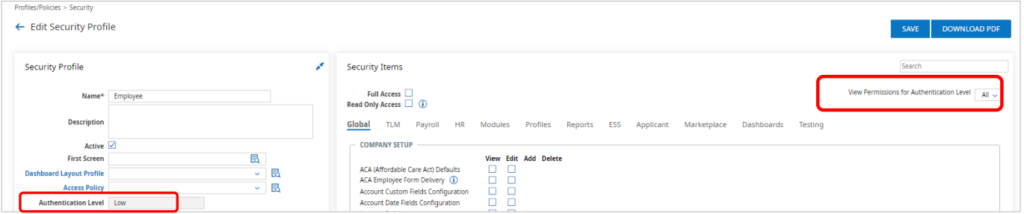
Security profiles are assigned authentication levels based on the permissions enabled for that security profile. There is a dropdown that filters the permissions based on the authentication level assigned.
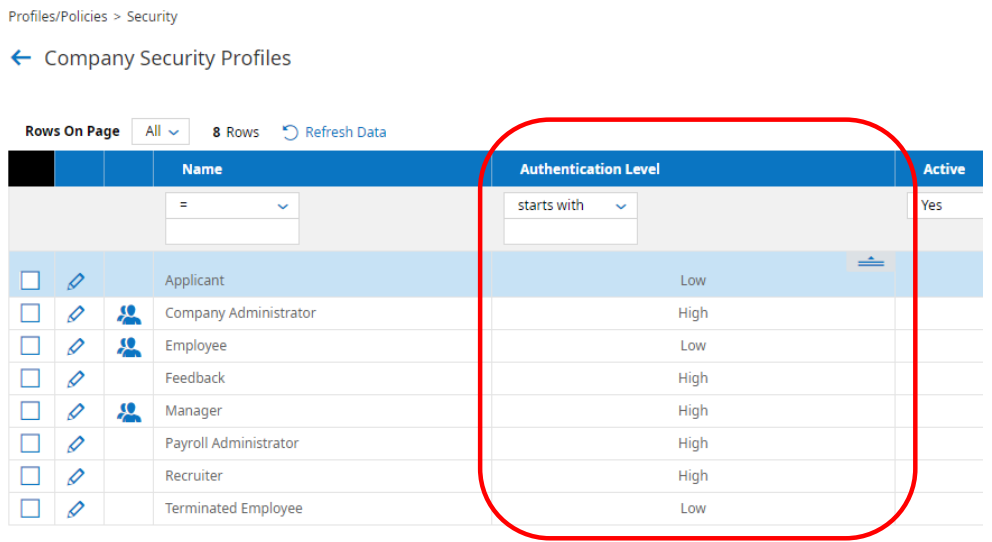
Company Security Profiles report includes the Authentication Level as an available column.
Authentication Level Assignment to the User
Authentication Level – User Assignment
Authentication level assigned to the user is reviewed and updated during the login process. If the user is registered for a two-factor option that is no longer applicable for the assigned authentication level
- The user will login with the current two-factor option
- All two-factor registrations will be cleared
- The user will be presented with the two-factor options and will be required to register
Note: If the user is assigned the low policy and is not required to two-factor, then they will be logged in. Authentication level is updated when the security profile assigned to the user is updated or when any fields are updated in the Account Information widget.
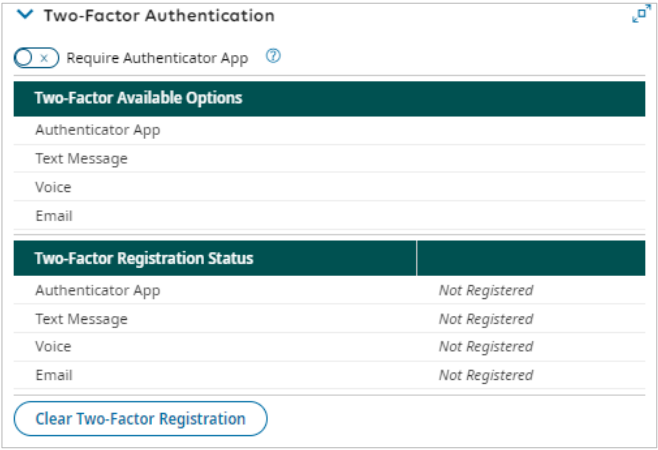
Two-Factor Authentication Employee Widget
- Allows the administrator to override the authentication profile and require Authentication App
- Displays the Two-Factor Options available to the user
- Displays the Two-Factor Registration Status
- Allows the administrator to clear Two-Factor Registration
Two-Factor Reports
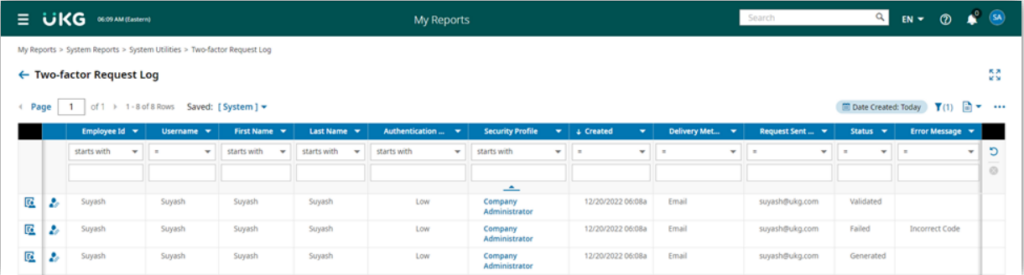
Two-Factor Request Log Report
Displays every two-factor request for all users.
Report includes:
- create date
- delivery method
- number or email address the code was sent to
- status of the request
- error messages
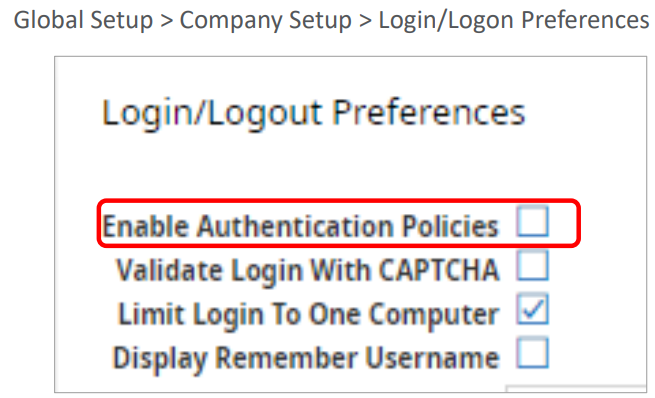
Enable the Password and Two-Factor Policies
Configuration option available to self-enable the new password and two-factor policies
- When selected low, medium and high policies are used
- When not selected, the legacy policy is used
UKG will enable for all customers in August, when UKG enables, this configure option will no longer be used.
Employee Experience
Two Factor Options
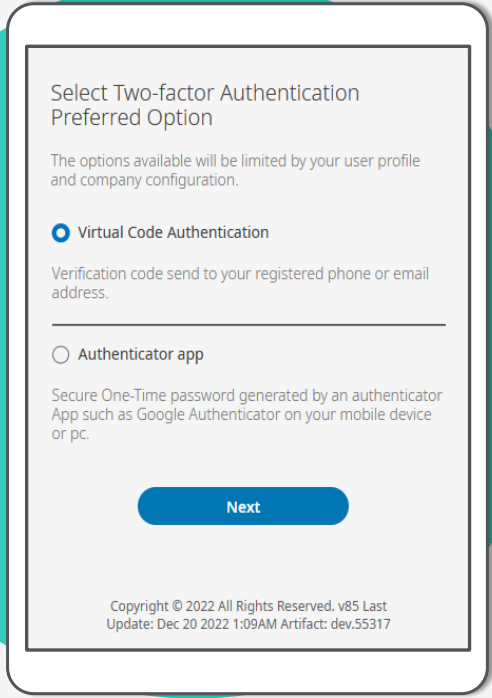
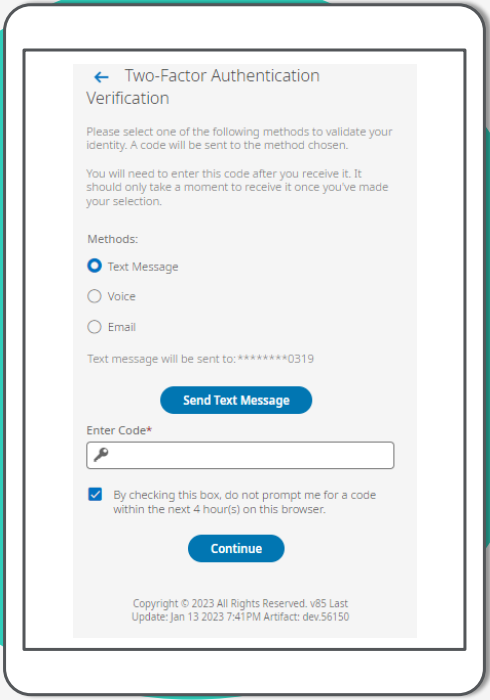
If Two-Factor options are not registered for the user, the Select Two-factor Authentication Option page is displayed for the user to select an option. Virtual code authentication and/or Authenticator app options are available based on the configuration in the authentication policy assigned to the user
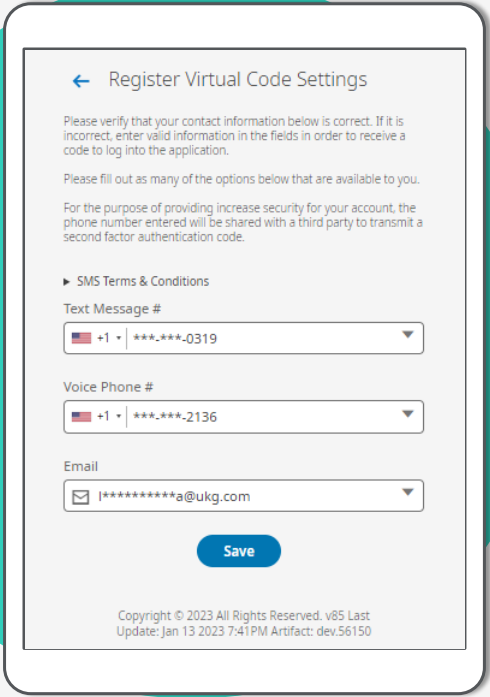
Virtual Code
If Virtual Code Authentication is selected the user is presented with the options available recommend the user selects the best value for all available options.
User selects a method and requests the code to be sent to that phone number or email address.
User enters the code received If they select the check box to remember device, the user will not be prompted for a code for the timeframe configured in the authentication profile.
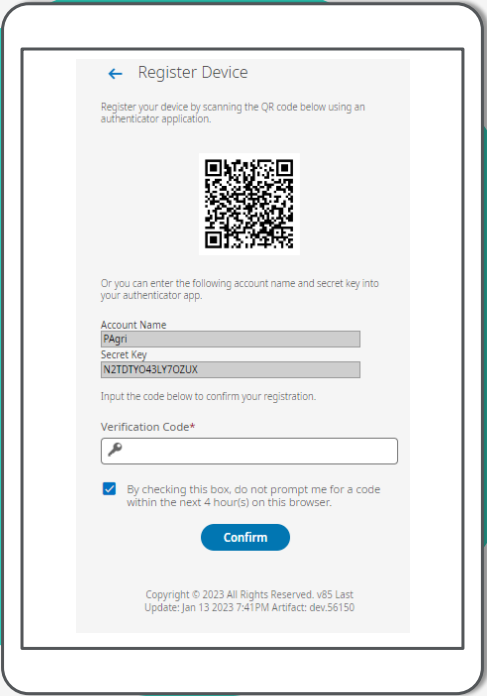
Authenticator App
User will register the device by scanning the QR code with their mobile device. User enters the code received. If they select the check box to remember device, they will not be prompted for a code for timeframe configured in the authentication profile.
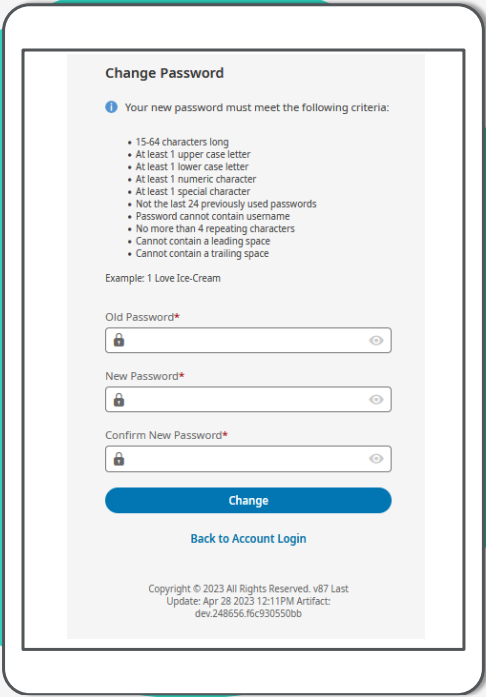
Change Password
Password is checked against the Maximum Password Age configured in the authentication policy assigned to the user. If password has expired, the user will be required to change their password. Hide/show icon available to allow the user to display the contents of each field.
Security Resources in Learning Center
How to access Learning Center
Log into your UKG Ready account > In your menu, navigate to My Info-> Help-> Learning Center -> Use the search bar to find your new learning journeys, courses, and job aids
MFA Change Management
Preparing for Change
Checklist for Success
✓ Single Sign-on (SSO)
✓ Understand Timing
✓ Get out in Front
✓ Identify Employee Groups
✓ Find what matters
✓ Plan and Communicate
✓ Embrace the “why”
✓ Response to challenges
Security Changes FAQ
What are the changes to the password requirements?
The following changes are being made to the password requirements within the system:
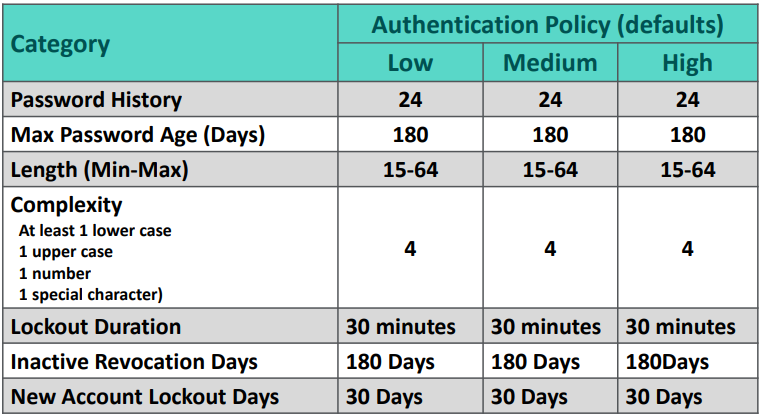
- Passwords need to be 15-64 characters long
- Password expires every 180 days. Can be updated to be more frequent
- Cannot reuse the last 24 passwords. Cannot be updated
Will my employees need to update their password when the changes are enabled?
When the employee logs into the application, their password will be analyzed and if it does not meet the password criteria, they will be redirected to the Change Password page to change their password to meet the new requirements.
What are authentication policies?
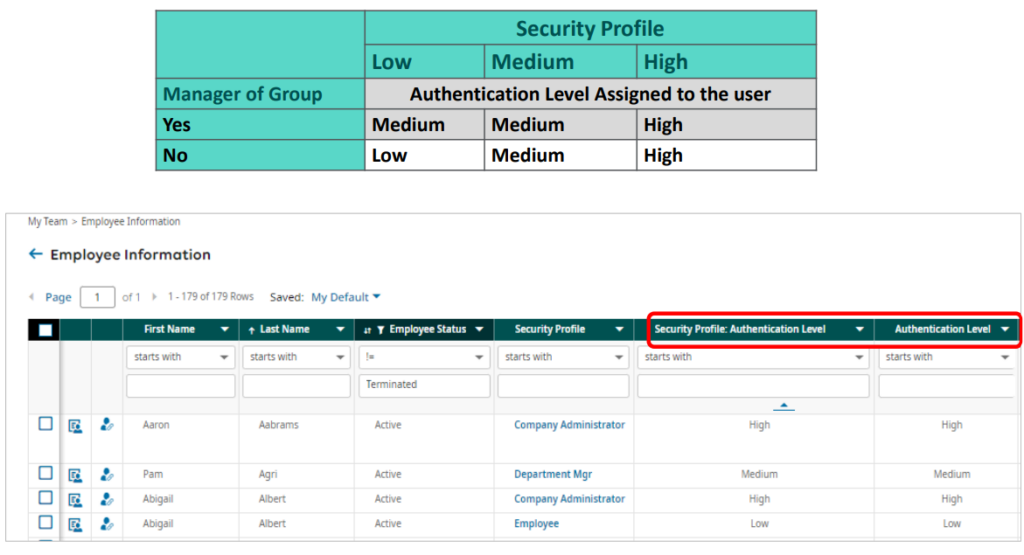
There are three authentication policies (Low, Medium, and High). The policies contain configurations for passwords and two-factor authentication. These policies are assigned to employees based on the security permissions they have and if they are a manager of an account group. The application will automatically assign the authentication policy levels to the employee. You cannot individually assign authentication policies to users.
What are the changes to the account lockout requirements?
- Users assigned the low authentication policy and locked themselves out will be locked for a minimum of 30 minutes.
- Users assigned the medium and high authentication policy and locked themselves out will need their account unlocked by an authorized user.
What are the changes to the inactive account lockout requirements?
- User accounts assigned the low authentication will have 30 days to log into the application for the first time before their account is locked.
- User accounts assigned the medium and high authentication will have 5 days to log into the application for the first time before their account is locked.
How can an administrator determine when an employee will be locked out?
The Employee Information report includes a new column, Inactive Days Until Locked. This column will display the number of days until the employee account will be locked unless they login.
How do I know which security profile permissions are aligned to each authentication policy?
Within each security profile there is a dropdown named “View Permissions for Authentication Level” on the right-hand side of the Security Items widget which allows you to filter by authentication policy level. This will allow you to figure out which security profile permissions are assigned to the authentication policies.
Can I create my own authentication policy?
Authentication policies are created by the application and a user cannot create additional ones. There are three authentication policies available (Low, Medium and High). The password policy and two-factor authentication policies within each authentication policy are configurable.
Can I assign all my employees to the high authentication policy?
Authentication policies are assigned by the application based on the permissions selected in the security profile assigned to the user and if they are a manager of an account group. You can modify the low and medium authentication policies to match the values in the high authentication policy.
What are the changes to the two-factor authentication requirements?
All users are required to use two-factor authentication when logging into the application. The authentication policy assigned to the user determines the frequency. By default, the frequency for users assigned to the low policy is 7 days, medium policy is 1 day, and high policy is 4 hours. This frequency assumes that the user has selected the remember device option.
What two-factor authentication options are available?
There are four options available for two-factor authentication. Test Message, Voice, Email, or time based one-time password (TOTP) authenticator app. Each authentication policy can be configured to provide any combination of the available options. By default, the low policy has all 4 options. The medium and high have Voice and time-based one-time password (TOTP)
In the future, for medium and high authentication policies, only Voice and time-based one-time password (TOTP) will be available. We strongly recommend configuring the Medium and High policies to only include these 2 options as soon as possible.
How can I determine which two-factor option my employee used at login?
The Two-Factor Request Log report is available that will include the two-factor option used, status, and other information about the request.
How do I know what two-factor options are available to my user and what they have registered for?
The Two-Factor Authentication widget in Employee Information shows what options are available and which options the user has registered for.
For new employees/accounts what are the password options
When there is an email associated to the new employee/account they will receive an email with their username and a unique password. If the user does not have an email address, the admin or hiring manager can provide a custom password that is configurable in each authentication policy.
Do users need to MFA when using the .clock page?
If the user is using the clocking in/out option, they will not be required to MFA. If the user logs in from this page, they will be required to MFA.
Do external applicants need to MFA?
No, external applicants using the .careers page will not be required to MFA. They will be required to adhere to the password policy requirements.
How are current accounts used for API’s affected?
If the accounts are only logging in using the API’s then they will not be affected. Once they log in through the user interface then their password will be required to be updated. Please note, that updating the password will require you to also update it within the integration you have set up otherwise the integration will break.
We highly recommend that you migrate those accounts to service accounts.
How do I migrate to service accounts?
You can migrate accounts to service accounts by going to the service account widget located in the company information/company setup page. Then type the username of the account that needs to be migrated assign it to an account group and press save. Migrated accounts will no longer be accessible through reports and will no longer have a profile. The accounts will also not be allowed to log in and can only be used for integration purposes. Once the account has been migrated, it cannot be reversed.